Biometrics. Bio meaning life, metric meaning measurement. Biometrics refers to the science of quantifying the human. In recent times, it is a hotly debated subject due to its use in access control. So, what kind of biometric techniques are there?
Fingerprints
Everyone’s got them, yet no two are the same. Those little swirls on the ends of your fingers can be quantified to generate a value that is unique to that digit, which is then used to authenticate it on a systems. How is this done? By looking at what’s known as minutiae.

Source: By Cyrillic at the English language Wikipedia, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=3335963
Fingerprints consist of three basic patterns (arch, loop, whorl). The above fingerprint is a whorl, where the fingerprint swirls around a central point. Interestingly, these three main archetypes are said to run in families, meaning that there may be a genetic element to fingerprint patterning.
Within the fingerprint, there are lots of tiny features; these are the minutiae. These include the ends of ridges, freestanding dots, and deltas (y-shaped ridges, like a river delta). These features can be detected by an image processing system, with their relative positions stored numerically. When another fingerprint is scanned, these values can be compared mathematically to calculate if it is a match or not.
Fingerprint scanners are commonly used because a lot of people are familiar with the concept, and so are somewhat accepting of it. They are also easy to use, both for the operator and the person being scanned. They are however prone to error if damage to the finger has occurred, and can be easily forged (depending on the quality of implementation, as will be discussed further later on). Depending on the implementation they may also require the user to physically place their finger on a scanning surface, which can lead to a inaccuracies from a build-up of skin oil if the system is not regularly cleaned.
Palm print
Much like our fingerprints, our palms also contain unique patterns.

Source: By Metrónomo – Own work, CC BY-SA 2.5 ar, https://commons.wikimedia.org/w/index.php?curid=28843764
These patterns are again unique to each hand. The different patterns making up the print can be quantified and stored similarly to how a fingerprint is. Palm prints are however much less common than fingerprints in the biometrics world because they’re a lot bigger, making them less convenient to collect (you’d need a bigger scanner, for one).
Vein matching
Although the general positioning of veins in humans is reasonably consistent, there is some space for variation. This means that vein matching can be used as a biometric technique.
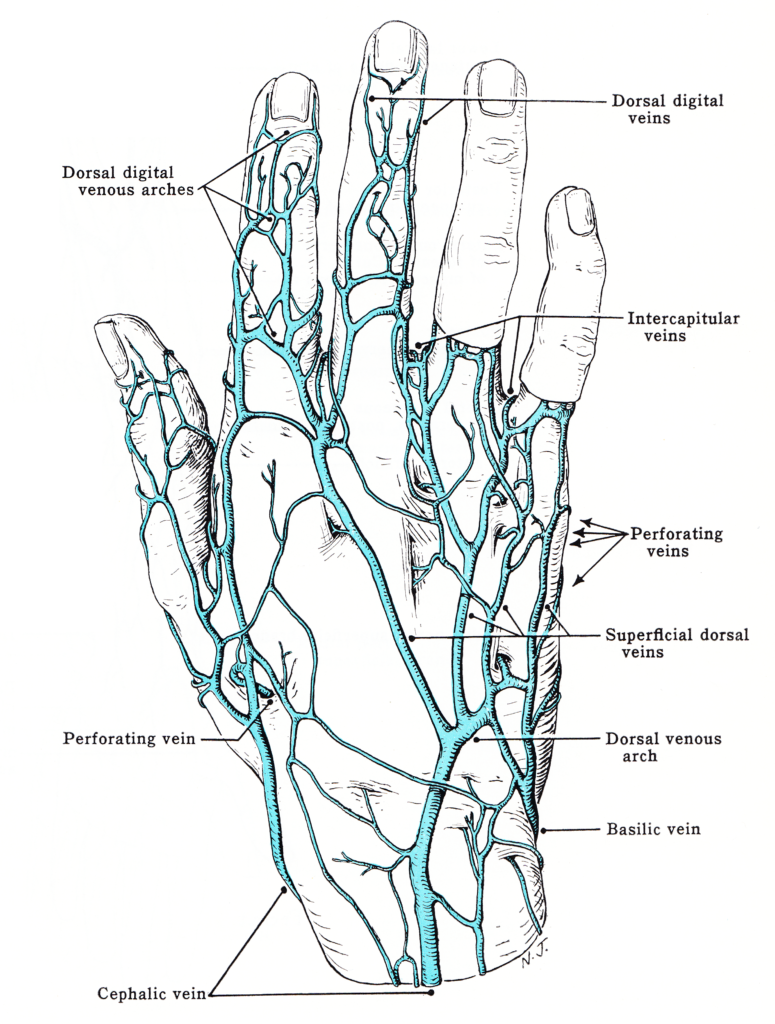
Source: https://upload.wikimedia.org/wikipedia/commons/5/57/Grant_1962_6.png
Images are generated by shining a very bright light on the target. In fingers and hands, a near-infrared LED is shone through the digital, with the haemoglobin in veins absorbing the light. This causes them to appear darker than the surrounding flesh in images taken.
In the case of eyes (for scleral eye vein biometrics), a standard light is shone on the target, and an image is taken from the same side. Because of the contrast of the eye veins to the surrounding whites, a regular high resolution image can be used. Eye veins are actually incredibly stable, not changing much with age, alcohol consumption, allergies, or other factors. As with some CCTV systems, infrared light can be used to light up the eye for image capture in low-light conditions.
People are frequently not comfortable with eye vein scans (as it requires light to be shone in to their eyes), and so hand/finger vein imaging is more commonly used.
Once the image of the vein positions has been captured it can then be quantified similarly to how fingerprint minutiae are, then used for future matching.
Hand geometry
The shape of the hand itself can be used as biometric measure.
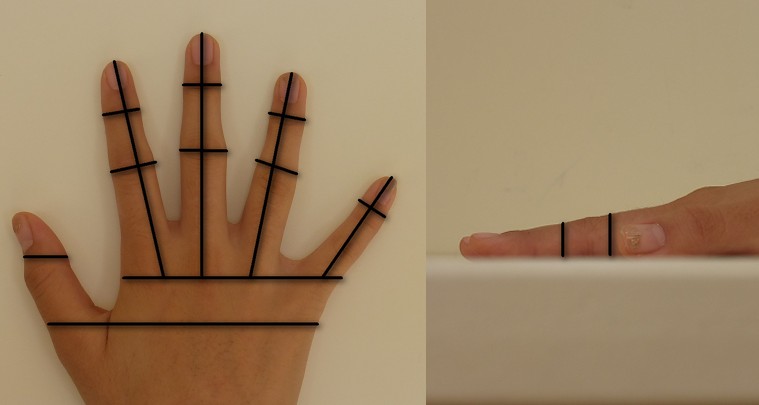
By Z22 – Own work, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=29938091
The above image shows some of the statistics that can be gathered about the hand. Visible hand geometry is fairly easy to see and collect, and so it was used a lot more in the early days of biometrics (dating as far back as the 1980s).
Hand geometry is a lot less individual than the measures mentioned above however, and so it is in infrequent use nowadays. It generally won’t be used in high security systems, although it can be used in addition to other techniques in multi-factor systems (more on this in a later!)
Interestingly, hand geometry gets used as a form of phrenology (the pseudoscience of measuring skull shape to predict mental traits) sometimes. I remember from school, kids telling me about how relative finger lengths can be used to discern someone’s sexuality. People seem to like trying to use facial recognition for this sort of thing, perhaps hand phrenology will become a thing! Alternatively, automated palm reading.
Iris recognition
A spy movie favourite, next up we have iris recognition. This involves quantifying all of the swirling patterns that may be present in a person’s iris.

By Smhossei – Own work, CC BY 3.0, https://commons.wikimedia.org/w/index.php?curid=11034706
Both regular visible light and infrared light may be used to take the image, depending on the application. Brown eyes (the most common eye colour in the world) tend to be less detailed in visible light, but rich in texture when near infrared light is used. An example near infrared image of a brown iris can be seen below.

Source: https://commons.wikimedia.org/wiki/File:IRiris.jpg
Iris images are an often-used biometric measure because they are relatively easy to collect, as well as being highly stable. Much like with eye veins, they don’t change depending on age or lifestyle. Fingerprints may end up partially obfuscated by scars over time, whereas this is much less likely with irises.
The collection of iris images can be a bit difficult, as it requires a person to get very close to a stationary device. As people tend to vary quite a bit in height, scanners can be seen as an annoyance to use. They are also very susceptible to spoofing attacks (more on this in a later post).
Retina scan
Another spy movie favourite, quite possibly because it sounds pretty cool.

Source: https://www.flickr.com/photos/hobbs_images/2590555768
Retina scans make use of the retina blood vessels in the eye. This differs from the previously mentioned scleral eye vein scan, which uses ones visible on the surface; the retina scan uses the reflection of a scanning infrared light to collect an image of the usually non-visible veins which adorn the back of the eyeball.
These veins, like other eye metrics, are highly stable (aside from in those suffering from disorders which directly affect this area, such as diabetes). Imaging of them is also reportedly highly accurate, with some claiming that it is the most accurate method of biometric scanning. Taking the scans however can be a bit of a faff, and the equipment required is very expensive.
Facial recognition
Facial recognition is an increasingly commonly used biometric technique, with various concerns arising through its proliferation.

There’s two main ways that facial recognition systems perform their matching: geometric, and photometric. Geometric facial matching can be seen in the above image, where key feature points in the face are picked out. These can then be stored much as fingerprint minutiae are. Photometric facial matching involved directly comparing images to images, using generated images such as Eigenfaces to perform the matches.

Source: https://commons.wikimedia.org/w/index.php?curid=442472
I’ve wrote a trio of blog posts on facial detection/recognition systems and how to defeat them, which can be seen here:
Part one: General concepts: https://www.vicharkness.co.uk/2019/01/20/the-art-of-defeating-facial-detection-systems-part-one/
Part two: Adversarial examples: https://www.vicharkness.co.uk/2019/01/27/the-art-of-defeating-facial-detection-systems-part-two-adversarial-examples/
Part three: The art community’s efforts to defeat these systems: https://www.vicharkness.co.uk/2019/02/01/the-art-of-defeating-facial-detection-systems-part-two-the-art-communitys-efforts/
Behaviometrics
Behaviometrics is the field of biometrics which are to do with a person’s behaviours, rather than an intrinsic statistic which describes an aspect of their physical being. The ways in which a person’s behaviours can be quantified are endless, but three of the most common techniques can be seen below.
Gait analysis
Gait analysis is the study of how people walk, run, or even stand.
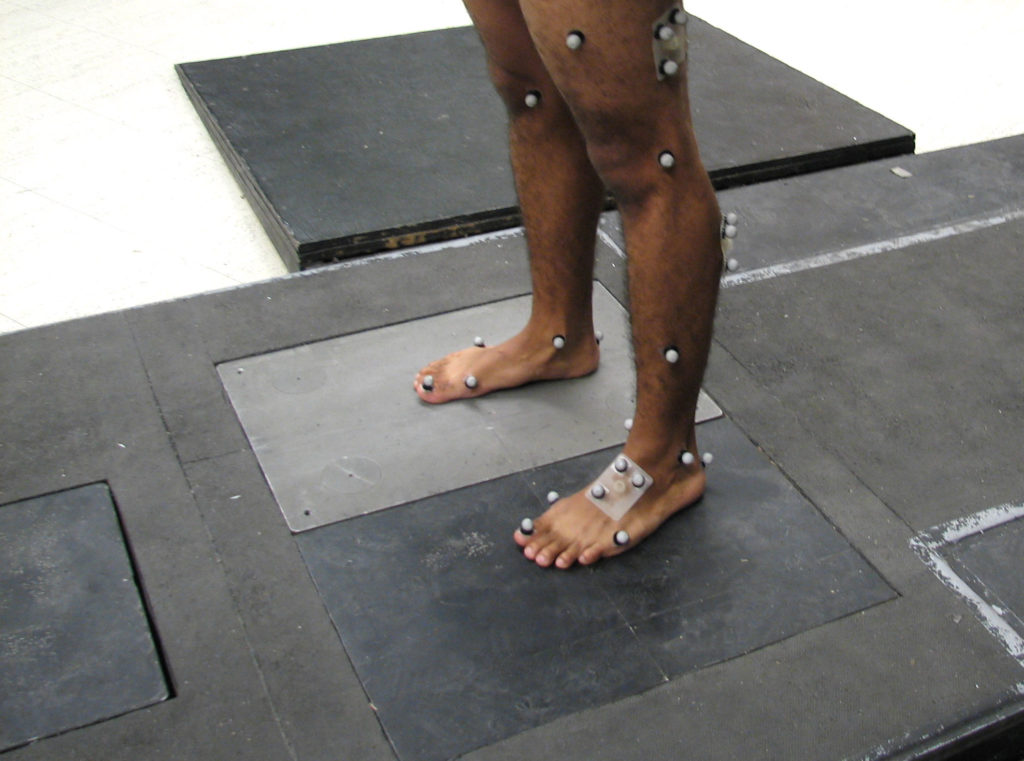
Source: By D. Gordon E. Robertson – Own work, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=6896127
Various points around the human body can be marked manually (or increasingly, through automated detect systems), which are then matched up to video feed of a person moving. By looking at how these points move relative to each-other, people can be identified through their gaits.
Gait analysis is something that seems to come naturally to humans. Without my glasses on, the world is one big colourful blur. In university I had a tendency to lose them, but learned to identify some close friends from a distance based solely on their walks. This is also something that people suffering from Prosopagnosia (face blindness) can find themselves using to identify people.
Gait analysis is a technique that is increasingly being used in public surveillance. It can not only be used to discern between people and track them, but it can reportedly also be used to identify nervous behaviours. Because of this, it is being introduced in to potential terrorist detection systems in some airports.
Voice recognition
“My voice is my passport”
Once again a popular sight in movies, this technique has been appearing in the real world a lot more in recent times. Voice recognition consists of converting a voice recording in to a visual image of the soundwave, and performing pattern matching on it. This is because currently, image processing techniques are a lot more advanced than raw audio processing. This methodology is used in a lot of audio processing systems, such as speech-to-text processors.
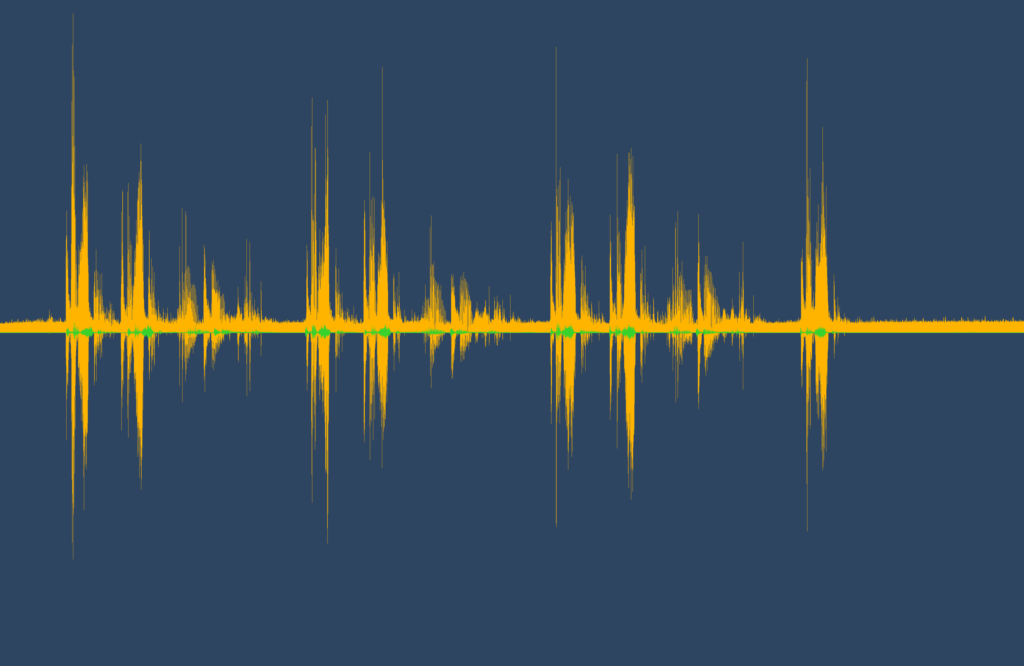
Source: By Gareth Halfacree from Bradford, UK – Andrea Electronics PureAudio Speech Development Kit, CC BY-SA 2.0, https://commons.wikimedia.org/w/index.php?curid=67172181
This method of authentication is increasingly being used in telephone banking systems. It’s very convenient as it can be performed automatically as a person speaks normally, but it is quite open to abuse (as the video clip shows). It is also susceptible to adversarial example-styled attacks, as was shown in a recent study by Nicholas Carlini and David Wagner: https://arxiv.org/abs/1801.01944
Keystroke dynamics
Keystroke dynamics refers to how a person types, rather than what they type. From sophisticated systems which analyse the pressure applied to keys through to simple systems which look at the typing rate/time between certain characters, there’s a whole lot of metadata which can be collected about how we type.
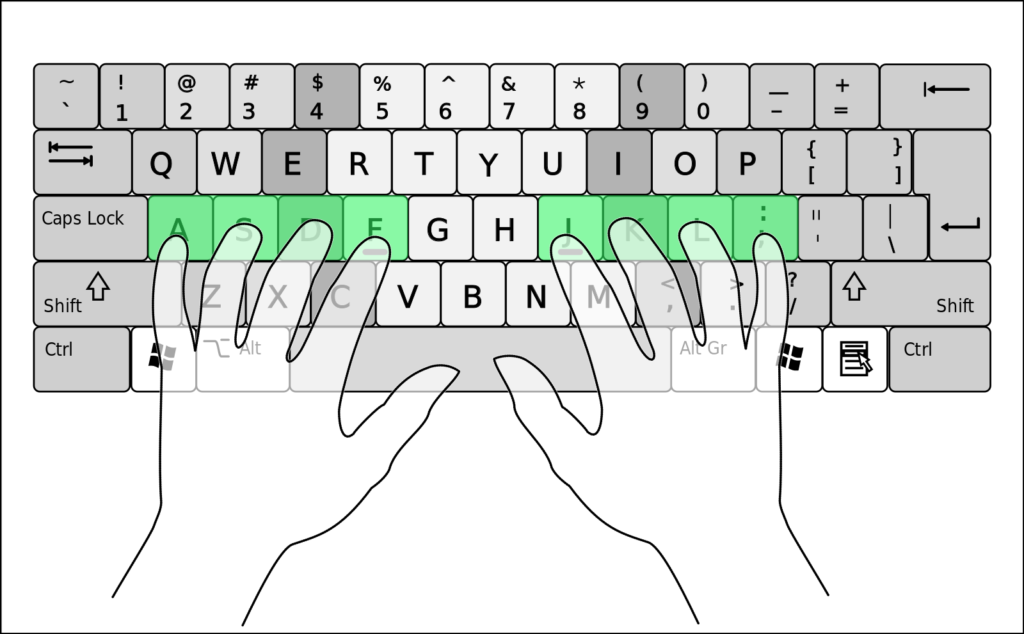
Source: By Cy21 – Own work, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=9666341
As with voice recognition, this can be used to authenticate a person discretely as they type. It can provide a secondary layer of authentication when typing a password, and is quite hard to fake. Choosing to use the hunt and peck method of typing over your regular touch typing will make an obvious difference, but it’s very hard to imitate the typing cadence of another person.
Multimodal biometrics
Most of these techniques are quite open to abuse when used on their own. How can this be avoided? Through the use of multimodal biometrics, of course!

Source: https://www.army.mil/e2/c/images/2018/03/01/508385/original.jpg
Take the example of an iris scan. Although an infrared version is harder to fake, some systems can be fooled simply by being provided by a photograph. The same goes for fingerprints. How can we avoid this?
One commonly used method is to perform a liveliness check (which never happens in the movies). If an automatic system is trying to authenticate based on an iris image, flash a bright light in to the eye to check if the pupil contracts correctly. If you’re scanning a fingerprint, perform a vein matching style scan to ensure that the target has a pulse.
In general, by using any type of two-factor authentication (2FA), you will increase the security of your system. This can be especially important in biometric authentication systems, as these tend to be in high security applications. Even just adding the use of a swipe access card or a password input to a biometrics system can dramatically increase the security. Lots of biometrics lend well to pairing- fingerprint and vein matching, iris and retina scanning. Pairing the recording of these biometrics from one location (i.e. a single eye, or a single finger) simultaneously makes them so much harder to fake.
There is of course the issue that you don’t want to be gathering too many pieces of biometric data about a single person. If your password is compromised, you just change it. It’s pretty hard to change a piece of biometric information. It also means that you will be using the same piece of information for multiple systems. If one location is compromised, it could induce a chain effect of compromises across all other systems that you are enrolled in.
Companies considering using biometric access controls? Think long and hard about your implementations (including if you actually need to be using biometrics), please!
Be First to Comment